February: Cyber Attacks in Southeast Europe
Hospitals, Power Plants, and Government Institutions in Crosshairs of Various Bad Actors
Southeast Europe is known for many things, but until a few years ago, cybercrime was still not one of them. In this blog, I will examine monthly activities of international cybercrime activity that affect the region, and try to create a chronicle of increasing attacks that bear the mark of renowned malicious actors.
This article specifically explores the cybersecurity incidents that occurred in February in Albania and Romania. Additionally, it offers a glance into a ransomware attack on Slovenia's critical infrastructure which occurred in late 2023.
As we navigate the aftermath of these events, the aim is to illuminate the context surrounding mounting incidents in the region, which often remain obscured in the fog of sporadic news coverage.
Without further ado, I bring you three separate cybersecurity news stories in the region that caught my attention in the past month.
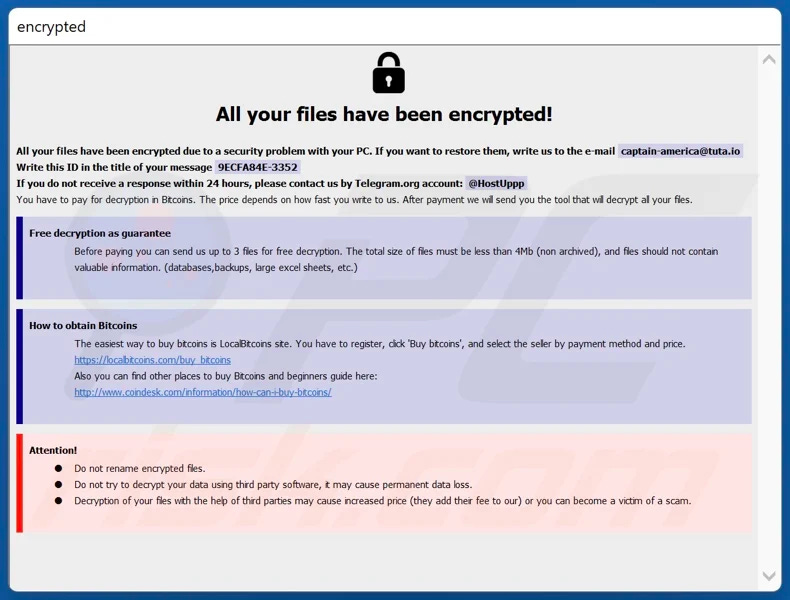
Over 100 Hospitals in Romania Knocked Out by Ransomware
In a distressing turn of events, more than 100 Romanian hospitals find themselves ensnared in the clutches of a ransomware threat, with Phobos group claiming the attack — a Russian-speaking entity renowned for exploiting vulnerabilities in the Remote Desktop Protocol for unauthorized access.
The bull's eye of the attack was the Hypocrite Information System, an integral IT management solution utilized by various healthcare institutions for managing patient data and other critical services. In response to the attack, medical personnel across the nation have resorted to the age-old practice of pen-and-paper, striving to maintain essential hospital functions.
The Romanian National Cyber Security Directorate (DNSC), in collaboration with cybersecurity experts from third-party entities, is actively engaged in investigating and containing the ongoing assault. However, as this battle unfolds, Romanian patients find themselves caught in the crossfire, their well-being hanging in the balance.
The cybercriminals behind this assault have set a hefty ransom of 3.5 Bitcoin, equivalent to over $164,500, in exchange for decrypting the vital files they've maliciously locked away.
While ransomware incidents targeting the healthcare sector are unfortunately not novel, it appears that the FBI's December 2023 crackdown on the ALPHV/BlackCat Dark Web infrastructure acted as a catalyst.
The aftermath has seen a surge in hospital-targeted attacks, not only in the US and Germany but now reaching Romania. The resilience of local authorities in handling such a crisis is yet to be fully gauged as the country experiences the full scope of a ransomware offensive.
Albanian Cybersecurity Under Siege: Iran-Backed Group Strikes Institutions
In the enduring shadow of Iran's geopolitical maneuvers, Albanian institutions face the looming and persistent threat of the country’s cyber warfare capacities. Air traffic control systems, Telco operators and government institutions have all fallen victim to the Teheran-backed Homeland Justice group in the past two years.
Most recently, on February 1, Homeland Justice executed a Wiper cyberattack on INSTAT, deleting crucial national data. The INSTAT cyber attack aimed to erase data and compromised as many as 40 computers, raising concerns about the integrity of sensitive information. A similar attack targeted the Albanian parliament at the end of 2023, though the official statement claimed there was no permanent data loss.
Homeland Justice’s motivation comes from Albania sheltering a shadowy Iranian opposition group, called the Mujahedeen-e-Khalq (MEK) and its 3,000 members. The MEK has been in Albania since 2013 and is a thorn in the side of official Teheran, which has turned to cyber pressure in hopes of arranging extradition of the group.
The group itself is reportedly unpopular in Albania – even more so – after the recent string of attacks. Yet Albanians are bound by the 2013 agreement brokered by the USA, which stipulates that MEK can remain in the country, under the condition of refraining from political activities and abiding by the nation's laws.
Stuck in limbo, the country braces itself, as Homeland Justice announces new attacks are inbound via its Telegram channel.
Rhysida Ransomware, Used in the Slovenian Power Plants Attack, Gets Decrypted: Is it a Little Too Late?
In November 2023, the notorious Rhysida ransomware targeted Slovenia's electrical infrastructure, specifically at the key holding company responsible for 60% of the nation's power production. Despite the potential for catastrophic consequences, the attack did not directly impact power production, although it did leave a lingering shadow that extended into 2024.
The aftermath raises questions about HSE Holding, the Slovenian power plant company, and how it dealt with the ransomware attack. Whether they paid the ransom, independently restored their data, or are still awaiting the recovery of parts of their infrastructure remains unclear.
If the last option is the case, and they are still affected, then a recent breakthrough might just be an answer to all their prayers.
Cybersecurity experts from Kookmin University and the Korea Internet & Security Agency (KISA) successfully cracked Rhysida's complex code. Exploiting an "implementation vulnerability" within the ransomware, they have provided a strong foothold against this digital threat in the form of free-to-use decryption software.
Whether or not this will be the silver bullet for Rhysida remains to be seen, as the group faces possibilities of mutation and resurgence or integration into emerging cartels like Lockbit and ALPHV/BlackCat.
Why is Southeast Europe Becoming a Hotbed of Cybercriminal Activity?
While the process of digitalization in the region has seen great growth, cybersecurity lags as a marginal effort in the overall digital culture. In short, progress occurs only after a cyber attack already happened.
Yet, relying solely on this reactive approach falls short of achieving robust security for organizations. Legal frameworks, both nationally and internationally, along with collaborative efforts, are still in their infancy. In turn, this offers additional maneuvering space for attackers.
Simultaneously, geopolitical motivations cast a shadow over the Balkans, enticing nation-state hackers to breach the digital defenses of vulnerable institutions for political pressure as seen between Iran and Albania.
In essence, the region is poised to remain a breeding ground for high-profile cybercrime attacks unless comprehensive strategies and substantial investments fortify the cybersecurity landscape. Achieving this feat will undoubtedly encounter numerous setbacks and will demand years of concerted effort, but it is what needs to be done if the region plans to counter the surging cyber risk demonstrated in the attacks listed above.
Did you like this article? Subscribe to Cyber Dispatch and follow me for more insights on the exciting cyber landscape of Southeast Europe.